1. 引言
在当今的数字时代,新兴的社交媒体如微博、脸谱等以及新发展起来的人工智能、智慧城市、物联网、无人驾驶汽车等技术给人们带来便捷服务的同时也给攻击者留下许多攻击的机会。如果个人敏感信息甚至有关国家安全的机密信息落入到不法犯罪分子手中,将会给个人和国家带来严重甚至是致命的影响,因此,信息安全问题就显得非常重要和迫切 [1] [2] 。数字图像因其具有直观、形象及生动等特点成为数字信息中最为广泛,也是最重要的一种信息表达形式 [3] 。因而对数字图像进行保护变得非常重要。现阶段对数字图像进行保护主要有两个方法 [4] ,即数字图像水印技术和数字图像加密技术。图像水印技术是为了保护图像的版权而在图像中嵌入可识别的不影响明文图像表达的水印,但其内容信息并不改变。图像加密又称图像隐藏,是指通过一个或一系列的可逆变换或映射把明文图像的明显特征进行隐藏,从而起到保护明文图像的作用。因而在现实生活中,图像加密是我们对图像进行保护的重要方法。图像因其自身的一些固有特性如数据量大、数据冗余度高和相邻像素相关性强等使得大部分的传统文本加密经典算法如DES (Data Encryption Standard)、AES (Advanced Encryption Standard)等不再适用图像加密 [5] ,因此,研究者们提出了大量不同于传统文本加密的算法对图像进行保护 [6] 。在这些算法中基于混沌理论的加密方法引起了人们地极大关注。混沌系统具有对系统初值和和参数的极端敏感性、伪随机性、状态遍历性等的混沌特性 [7] [8] ,正因为这些性质与密码学中的典型要求非常契合,如混沌系统对参数和初值的极端敏感性和加密系统对密钥极端敏感之间的对应、混沌的拓扑传递性和混合特性与加密系统的扩散之间的对应等,因而利用混沌系统来设计图像加密算法具有很好的应用前景 [9] [10] [11] [12] 。
自从1989年英国学者Matthews在文献 [10] 中将混沌理论引入加密研究领域以来,就有大批的学者涌入基于混沌的图像加密研究中。1998年,Fridrich利用二维混沌系统提出了基于置乱–扩散结构的图像加密算法 [11] ,在置乱过程中,首先利用二维混沌系统对明文图像的位置进行置乱,然后在扩散过程中利用一维混沌系统产生的伪随机序列扩散置乱后的像素灰度值。基于置乱–扩散机制的算法占据现有图像加密算法的重要比例 [12] - [22] 。文献 [4] 采用SP (Substitution-Permutation)结构提出了一种基于简单非线性替代的图像加密算法,代替阶段采用依赖于随机密钥的非线性迭代变换来完成,其中所用的密钥由离散混沌系统产生,而在置乱阶段则利用变量函数化的方式,引入两个一维混沌映射来构造出新的二维映射来对数字图像的位置进行置乱。该算法巧妙地构造出具有良好随机特性的二维混沌映射对图像进行加密,具有对密钥空间大、密钥敏感性强等特点。文献 [12] 提出基于耦合Logistic的对称图像加密算法。该算法改变传统的置乱–扩散加密机制,采用了预先取模–置乱–扩散的结构,即先对明文图像以按行按列的方式做预先取模运算,然后利用耦合的一维混沌映射产生随机数依按行按列地对预先进行取模运算后的图像做周期移位,最后通过取模运算对置乱后的图像进行扩散产生密文。这篇文章设计的算法密钥产生依赖于明文,改进传统的置乱–扩散结构,先采用像素灰度值的预先取模再进行置乱–扩散的结构很好地克服了明文图像的两个或多个比特位改变后像素灰度值总和仍不改变的这一安全隐患,并且该算法能够很好地抵抗统计攻击等,该算法的两个扩散过程更是使得像素扩散的速度加快,更有利于保护图像信息。文献 [13] 利用两个被研究得比较透彻的一维混沌映射构造了一个新的二维混沌映射(2D-SLMM, 2-dimensional Sine Logistic Modulation Map),并且基于新的二维映射提出一种快速图像加密算法。该算基于2D-SLMM设计了混沌转换变换(CMT, Chaotic Shift Transform)对明文图像的像素位置进行置乱,该置乱方法仅置乱一次就能够把明文图像平面内任意一个像素置乱任意位置。在扩散阶段,利用2D-SLMM产生随机数对置乱后的像素灰度值通过取模运算进行扩散。该算法巧妙地设计置乱算法和反馈式的扩散机制使得加密效果优于许多其他现存的算法。文献 [14] 提出混合比特位置乱和基于混沌系统的彩色图像加密算法。该算法依据任意一幅自然图像不同比特位平面占据不同明文信息的差异性设计了混合比特位的置乱,这样做可以大大地减少了计算成本和提高了置乱效果。在扩散阶段应用广义的异或运算对彩色图像的各颜色通道进行扩散,从而使得算法的加密效果更优。文献 [15] 提出基于多混沌系统的彩色图像加密算法。该算法反复利用广义的Arnold映射产生随机数对明文彩色图像进行置乱和扩散,其中采用依行依列的方式对置乱后的图像进行扩散,大大地加快了加密的速度。文献 [16] 提出基于混合超混沌系统和元胞自动机的数字彩色图像加密算法。该算法为克服元胞自动机(CA, Cellular Automata)理论在加密应用中不能产生长序列等不足提出一种非一致元胞自动机(Non-uniform CA)并利用该自动机设计图像加密算法。彩色图像加密算法采用置乱–扩散机制,在置乱阶段用超混沌系统产生的混沌序列对明文彩色图像的各个颜色通道进行像素位置的置乱,而在扩散阶段则采用改进的元胞自动机产生密钥矩阵对置乱后的图像进行扩散。该算法成功地运用二维元胞自动机对图像进行加密,使得数字图像加密的方法更丰富。文献 [17] 和 [18] 分别利用物理学领域中的导出回转器变换(Deduced gyrator transform, DGT)和多脉冲注入技术(Multiple impulse injection)的一些特性对数字彩色图像信息进行隐藏,更是大大地开阔了设计图像加密算法的思路,使得图像加密这一领域的理论基础更加完善。
文献 [19] 利用混沌理论中一些经典一维混沌映射如Logistic映射和Sine映射等的输出差异性构造出新的一维混沌映射,使得新一维混沌映射比原来的映射有更大的混沌区间和更好的混沌性质,并且基于新构造的一维混沌映射设计了一种新的彩色图像加密算法,该算法首先将三维的彩色图像矩阵转化成二维图像像素矩阵,在置乱阶段利用新构造的一维混沌映射系统产生伪随机序列,并以降序的顺序排序获得序列的相对位置,然后利用获得的相对位置对二维图像矩阵进行像素的位置置乱,在扩散阶段,应用取模运算和按位比特位异或运算对置乱后的像素灰度值进行扩散加密,有一定的加密效果。但是加密算法结构简单,易于被攻击,有待加强复杂性。文献 [20] 提出基于标准映射的彩色图像加密算法。该算法反复地利用离散的标准映射产生随机数对明文彩色图像进行依行依列的置乱扩散,具有良好的加密效果。但在整个算法中只运用了离散标准映射一种混沌系统,根据文献 [9] ,整个算法的安全性有待提高,并且离散标准映射的参数空间只有一个参数组成,即参数空间小,这对于图像加密来说无疑是一个安全隐患。因此,根据以上分析与总结,本文利用标准映射的结构,对其变量的进行函数化,引入改进的两个一维混沌映射构造出一种新的二维映射,称为类标准映射。构造出来的新类标准映射仍然是一个混沌系统,并且其参数空间比标准映射的参数空间要大、产生的混沌序列更加难以预测。然后提出基于一维混沌映射和类标准映射的彩色图像加密新算法,算法采用预先扩散–置乱–扩散对称结构,利用两个一维混沌系统对明文彩色图像进行预处理,这样可以避免同时改变明文图像像素灰度值的一个比特位值或多个比特位值后不改变像素灰度值总和的安全隐患发生。然后利用新构造的类标准映射产生伪随机数对预处理后的图像进行置乱–扩散加密。
本文的结构如下,在第1节,介绍改进的一维混沌映射和类标准映射的构造。首先简单地介绍由经典混沌映射产生的新一维混沌映射,简单分析其动力学性质,然后阐述类标准映射的构造及其混沌特性分析。在第2节提出基于改进一维混沌映射和类标准映射的图像加密算法。对于本文提出算法的仿真实验和加密性能分析在第3节被提出,最后在第4节给出本文总结。
2. 前期准备
在这一部分,简单地介绍与本文有关的主要混沌系统。首先,由文献 [19] ,引入两个一维混沌映射LLS (Logistic-Logistic System),SSS (Sine-Sine System)。这两个新的一维映射比经典混沌一维映射具有更大的混沌区间和混沌特性更好等优势。然后根据文献 [4] 和引入的一维混沌映射构造出一个新的类标准映射,最后对新构造类标准映射的动力学行为进行分析,包括相位空间图、Lyapunov指数曲线变化图、时间序列分析等。
2.1. 一维混沌系统
一维混沌映射由于其简单的拓扑结构而广泛地被应用在图像加密领域。在混沌动力系统中,经典的一维混沌映射有Logistic映射、Sine映射和Chebyshev映射等,把这些映射应用在数字图像加密中存在混沌区间有限即参数空间有限、混沌输出序列的数据序列分布非一致等不足。为了解决这些问题,文献 [19] 基于这些经典一维映射的混沌序列输出差异性构造出一类新的一维混沌映射,使得新构造的混沌映射具有更大的混沌区间和更优的混沌特性。其中,基于这种构造方法和Logistic映射、Sine映射得到了两个新的一维映射LLS,SSS,其数学公式定义如下:
(1)
(2)
其中
是系统参数。由文献 [19] 容易知道上述两个一维混沌系统在参数区间上混沌的,在图1分别画出了LLS,SSS在参数空间上的空间相位图,很明显,它们在整个区间上是处于混沌状态的,因而新构造的一维混沌映射LLS,SSS的混沌特性比Logistic映射和Sine映射更优。
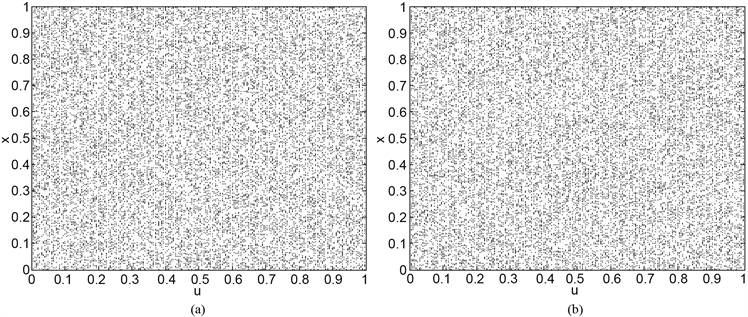
Figure 1. (a)-(b) are spatial phase diagrams of LLS and SSS, respectively
图1. (a)-(b)分别为LLS,SSS的空间相位图
2.2. 类标准映射的构造
标准映射(Standard Map),又称为Chirikov标准映射,它是一种从边长为2π的正方形区域到它自己的保面积映射,它反映了弹跳球模型在高弹跳情形下的二维映射,其数学公式定义如下:
(3)
这里
是满足大于0的系统控制参数,
位于
方形区域。图2(a),图2(b)分别画出了取不同参数
对应的空间相位图,从图中可以看到,不同参数甚至仅相差微小部分对应的相图差别较大,从而标准映射的动力学行为极其复杂。为了使用标准映射对图像进行加密,文献 [11] 对标准映射行
了从边长为2π的正方形区域离散化到以正整数
为边长的方形格子,即:令
,
,
,则标准映射可变为:
(4)
这里
为系统参数。
对于离散混沌系统(4)进行推广,即把变量函数化,可以得到如下含变量的数学公式:
(5)
基于文献 [4] 和以上的讨论,利用两个新一维混沌映射LLS,SSS的良好混沌特性,构造出一种新的类标准映射,其数学公式定义如下:
(6)
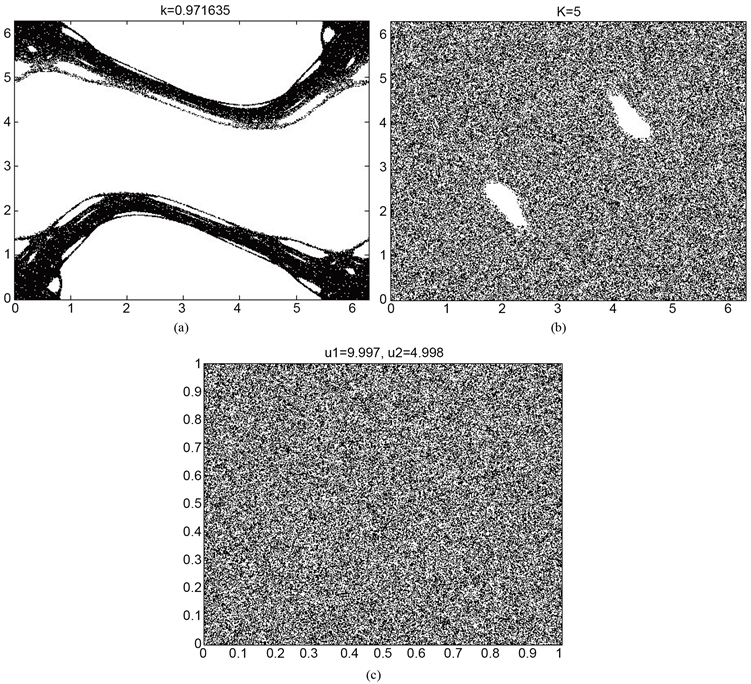
Figure 2. (a)-(b) are the phase map of the standard mapping parameter k at 0.971635 and 5 respectively, (c) is the phase map of the quasi-standard mapping
图2. (a)-(b)分别为LLS,SSS的空间相位图,(c)为类标准映射的相位空间图
这里
,
为类标准映射的系统参数,在理论上其取值范围可以取到无穷大,但在本文中
,
的范围均取为
。
为了说明本文提出的类标准映射具有良好的混沌特性,下面就空间相位图、Lyapunov指数和时间序列测试三个方面考察新类标准映射的混沌特性。首先,一个混沌系统的空间相位图可以直观地观察到其动力学行为演化的过程,图2(c)画出了类标准映射的空间相位图,可以发现,类标准映射在整个相平面上是处于遍历状态的,从而说明混沌特性优良,产生的序列难以被预测,这对于设计图像加密算法来说是有利的。其次,Lyapunov指数是指在动力学演化过程中相互靠近的两条轨道随着时间的变化,轨道之间以指数分离或聚合的平均变化率。在图3画出了类标准映射两个参数的Lyapunov指数变化曲线图,通过取定初值和其中一个参数,控制另外一个参数变化得到相应的Lyapunov指数。从曲线图可以观察到,类标准映射(QStd, Quasi-standard)的两个参数均有一个大于0和一个小于0的Lyapunov指数,从而可以说明新构造的类标准映射在参数区间上是混沌的。时间序列分析是对混沌系统产生的时间序列进行统计
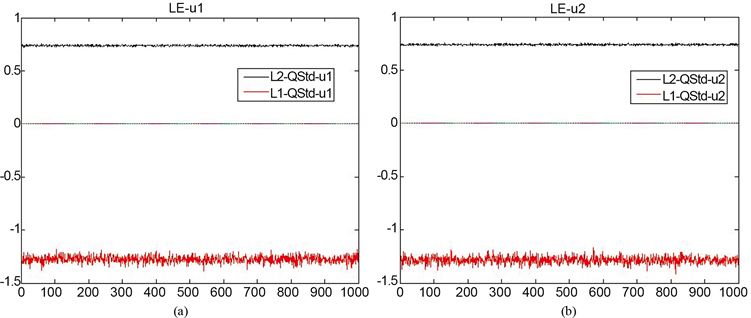
Figure 3. (a)-(b) are the Lyapunov exponent curve of the two parameters of the quasi-standard mapping
图3. (a)-(b)分别对应类标准映射的两个参数的Lyapunov指数变化曲线图
分析,用统计的方法进行研究分析,寻找其变化规律,从而判断对未来的情况进行预测、决策和控制的可能性大小。为了更进一步说明类标准映射具有较好的随机性质和不可预测性,本文测试了类标准映射产生时间序列的相关性,其中自相关性系数和互相关系数是两个主要的度量指标。对于两个随机时间序列
,
,它们延迟
阶的互相关性系数(crosscorr)和延迟
阶的自相关系数(autocorr)的数学公式定义分别如下:
(6)
(7)
这里
指的是序列
的算术平均值。图4是类标准映射两个变量的伪随机序列变化图,图5是类标准映射产生伪随机序列的自相关性和互相关性测试结果。从测试结果可以看到,混沌序列的自相关和互相关性均在0上下波动,这说明类标准映射产生的序列具有很强的随机性,因而具有不可预测性等好的密码特性,特别适合用于设计加密算法。
3. 基于一维混沌映射和类标准映射的图像加密算法
基于以上的结果和分析,在这一节设计一种基于一维混沌映射和类标准映射的数字彩色图像加密新算法。这个算法采用不同于传统模式的预先扩散–置乱–扩散结构。在明文图像的预处理阶段,利用LLS,SSS产生两个初始向量对明文图像进行预处理,这样可以大大地提高算法抵抗已知明文和选择明文的能力。在置乱–扩散阶段,先利用本文提出的类标准映射产生伪随机数对预处理后的明文图像的像素位置进行依行依列的置乱,然后使用不同初值和参数的类标准映射构造出2个不相同密钥矩阵,并利用它们按照动态反馈的方式来对置乱后的像素灰度值进行扩散产生密文。在这个算法中,采用依行依列的方式对明文图像进行加密,这样可以增大加解密速度。不失一般性,不妨记明文图像为
,且其大小为
,
,
为彩色图像颜色通道的像素灰度值矩阵大小,
为彩色图像颜色通道的数量,即
,本文提出的加密算法详细步骤如下:
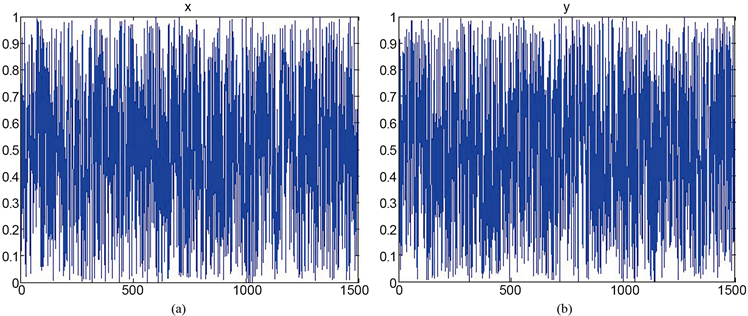
Figure 4. (a)-(b) are the x, y time series change graphs of quasi-standard mapping, respectively
图4. (a)-(b)分别是类标准映射的x,y时间序列变化图
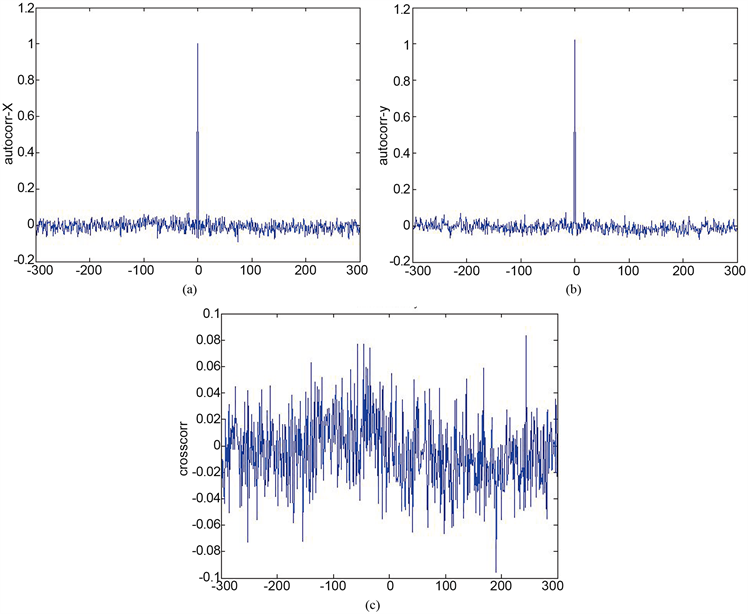
Figure 5. (a)-(c) are the auto-correlation and cross-correlation test results of the quasi-standard mapping time series, respectively
图5. (a)-(c)分别为类标准映射时间序列的自相关性和互相关性测试结果
Step1 读取明文,输入密钥。读入明文彩色图像
,并记
;输入混沌映射的参数
、
、
,为了避免过渡效应发生的预先迭代步数
,一维混沌映射的初值
,
。另外,把3维明文彩色图像
按从上到下、从左到右的顺序拉成大小为
的2维图像矩阵
,理论上为了加密算法具有更快的速度,应该尽量使
是方形图像矩阵,即要满足
和
最小。在本算法的仿真实验中,取
,
。
Step2 产生两个初始向量
,
。首先依据输入参数
和初值
,
对LLS,SSS分别迭代
,
次产生两个一维向量
、
,为了避免量化过程过渡效应的发生,把
,
的前
项丢弃,并且把丢弃
项后的
拉成一个列向量,这样就得到两个新的向量
,
,大小分别为
,
。最后利用如下数学公式(8),(9)产生一个初始行向量
和一个列向量
。
(8)
(9)
Step3 对
按行进行预处理。设置
的取值为1到
,令初始行向量
的每个元素向右周期移动
位产生与
相同大小的
,然后依据如下式(10)对
进行预处理产生
。
(10)
Step4 对
按列进行预处理。同样地,让
的取值为1到
,令初始列向量
的每个序列值向下周期移动
位产生与
相同大小的
,然后根据如下式(11)对
做预处理运算,最终产生预处理图像
。
(11)
Step5 计算类标准映射新的初值和新的整数值
。首先计算
的像素灰度值总和,并且记为
,然后利用如下式子(12),(13),(14),(15)分别计算出初值
,
,
。
(12)
(13)
(14)
(15)
Step6 计算坐标索引向量
,
,
,
。首先依据初值
,
和参数
,
迭代类标准映射
次产生两个伪随机序列,并分别把前
个迭代值丢弃得到两个新的伪随机序列
,
。采用
和
的前
个对应元素的算术平均值来产生新的向量
,其大小为
,类似地,采用
,
的对应元素的几何平均值产生另外一个新的一维向量
,其大小为
。最后通过如下(16),(17),(18),(19)得到坐标索引向量
,
,
,
。
(16)
(17)
(18)
(19)
Step7 对预处理后的图像进行置乱。设置
的取值为1到
,让 的第
行和第
行互相交换,然后令
的取值为1到
,让
的第
列和
第
列互相交换得到置乱图像矩阵
。
的第
行和第
行互相交换,然后令
的取值为1到
,让
的第
列和
第
列互相交换得到置乱图像矩阵
。
Step8 构造密钥矩阵
,
。利用与Step6相同的参数值和序列 ,
的最后一项作为类标准映射新的初值并对其迭代
次,将前
个序列值丢弃得到两个大小均为
的序列
,
,通过如下(20),(21)式进行量化并把两个一维向量分别按从上到下、从左到右拉成2维密钥矩阵
,
。
,
的最后一项作为类标准映射新的初值并对其迭代
次,将前
个序列值丢弃得到两个大小均为
的序列
,
,通过如下(20),(21)式进行量化并把两个一维向量分别按从上到下、从左到右拉成2维密钥矩阵
,
。
(20)
(21)
Step9 对
按行做扩散运算。首先把初始行向量
添加到
的最后一行,此时的矩阵仍记为
。设置
的取值为1到
,计算
的第
行到最后一行所有像素灰度值的和,记为
,然后采用式(22),(23)对
进行按行扩散得到
。
(22)
(23)
Step10 对
按列做扩散运算。把
最后一行丢弃并把初始列向量
放到
的最后一列,记上述操作后的图像为
。类似于Step9,让
的取值为1到
,计算
的第
列到最后一列所有像素灰度值和,记为
,然后通过式(24),(25)对
进行扩散操作得到密文
。
(24)
(25)
注:上述加密过程中,
是指实数
除以实数
得到的余数,
是指对实数 的四舍五入取整函数,
返回不超过实数
的最大的整数,
返回的是实数
与实数
的按位异或运算结果,
是指对实数
的取绝对值运算,
返回大于实数
的最小整数,
是指矩阵
的第
行元素,
是指矩阵
的第
列元素,
是指序列
的最后一项。本文提出加密算法的流程图如图6所示,解密过程是加密过程的逆过程,即采用相同密钥做逆运算,详细步骤这里不再赘述。
的四舍五入取整函数,
返回不超过实数
的最大的整数,
返回的是实数
与实数
的按位异或运算结果,
是指对实数
的取绝对值运算,
返回大于实数
的最小整数,
是指矩阵
的第
行元素,
是指矩阵
的第
列元素,
是指序列
的最后一项。本文提出加密算法的流程图如图6所示,解密过程是加密过程的逆过程,即采用相同密钥做逆运算,详细步骤这里不再赘述。
4. 本文提出算法的仿真实验和加密性能分析
4.1. 仿真实验
在这一部分,采用Matlab R2014a软件对本文提出的彩色图像加密新算法进行仿真测试。本文所有的实验均在同一台个人计算机上实现与执行,计算机的主要硬件环境如下:CPU处理器:Intel(R)Core(TM)
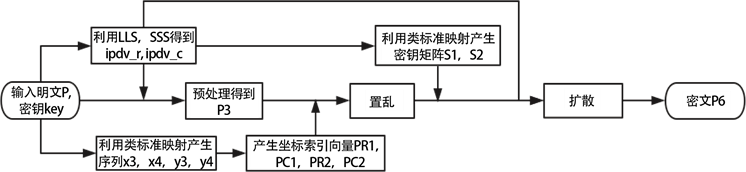
Figure 6. The flow chart of the encryption algorithm proposed in this paper
图6. 本文提出加密算法流程图
i7-5500CPU@2.40GHz 2.39GHz,安装内存:4.00GB;计算机运行系统:Windows 8.1中文版。另外,所有的仿真实验图像都是取自文献 [23] 的图像数据库。采用的加密密钥为
分别对三幅尺寸大小均为
彩色图像即Lena,Tiffany,Mandrill用本文提出的加密算法进行加密,其结果如图7所示,可以观察注意到,所有的密文均呈现“雪花”形状且无明显纹理出现,展现出完全混乱的现象,攻击者不能从密文中获取任何有关密钥和明文图像的信息,因而对明文图像起到了很好的保护作用,这说明了本文提出的彩色图像加密算法有一个非常好地加密效果,而且所有的密文都可以通过正确的加密密钥来获得与明文完全相同的图像。
4.2. 加密性能分析
一般来说,一个安全性强的图像加密算法能够抵抗绝大多数的已知攻击,比如已知明文或选择明文攻击、选择密文攻击、仅知密文攻击和各种蛮力攻击等。为了检验本文提出加密算法的安全性强弱,对于图像加密算法的重要安全分析如密钥空间分析、统计分析、密钥敏感性分析和差分分析等均在这一小节讨论。
4.2.1
. 密钥空间分析
加密算法的密钥空间是指能够用在加密过程中的密钥所有可能取值的总和。如果一个加密算法的密钥空间不足够大,很多非法攻击如暴力攻击等非常容易地对加密算法进行破解,因此加密算法安全性强的必要条件是必须要有足够大的密钥空间。从今天计算机的计算精度来看,对于普通加密的实际应用中,大于128 bit的密钥空间一般被认为是安全的 [20] 。在本文提出的加密算法中,如果把算法的密钥空间定义为由
组成的空间大小,其中,
,
,
,
,
分别为混沌映射的参数和初值,
是为了避免产生过渡效应的预先迭代次数,为了不增加计算的时间,一般取其量级为104。如果取双精度数据的精度作为计算,那么可以得到本文提出算法的密钥空间大小,即
,这个值远远大于理论值128 bit,而且,如果把混沌映射的其他初值和参数也作为密钥的组成部分,那么本文提出算法的密钥空间将会变得更加大。这就说明了本文提出的彩色图像加密算法具有非常大的密钥空间,它足以抵抗各种暴力攻击。
4.2.2
. 直方图分析
一幅图像的一维直方图是表示图像灰度分布情况的统计图表 [24] 。一般地,一维直方图的横坐标表示灰度级,纵坐标则表示具有该灰度级的像素个数或者出现这个灰度级的概率或频率。由于每个像素灰度级对应的概率或频率给出了对该灰度级出现的概率估计,因而直方图提供了图像的像素灰度值分布情况,即给出了一幅图像所有灰度值的整体情况描述。对于一幅8比特的灰度图像,其灰度值可能有28种不同
的取值,因此,灰度图像的直方图显示了256种不同灰度值的分布情况。对于一个安全性强的图像加密算法,加密得到的密文图像的灰度值应该有一致分布的趋势。对于一幅数字彩色图像,则将其红、绿、蓝颜色通道各看作是特殊一幅灰度图像,这样就可以用灰度图像的一维直方图方法去分析加密算法的性能。图8分别画出了Lena明文及其密文红、绿、蓝3个颜色通道的一维直方图,可以看到,密文图像各颜色通道的直方图均比明文图像对应的颜色通道的分布更加平坦,基本趋于一致分布,波动范围较明文图像各颜色通道要小,这也就说明了本文提出的算法具有良好的鲁棒性。
4.2.3
. 信息熵分析
在信息论中,信息熵是反映一个信息源的随机性和不可预测性的数学概念。对于数字图像来说,信息熵则反映了图像信息的不确定性。一个信息源m的信息熵
数学公式定义如下:
(26)
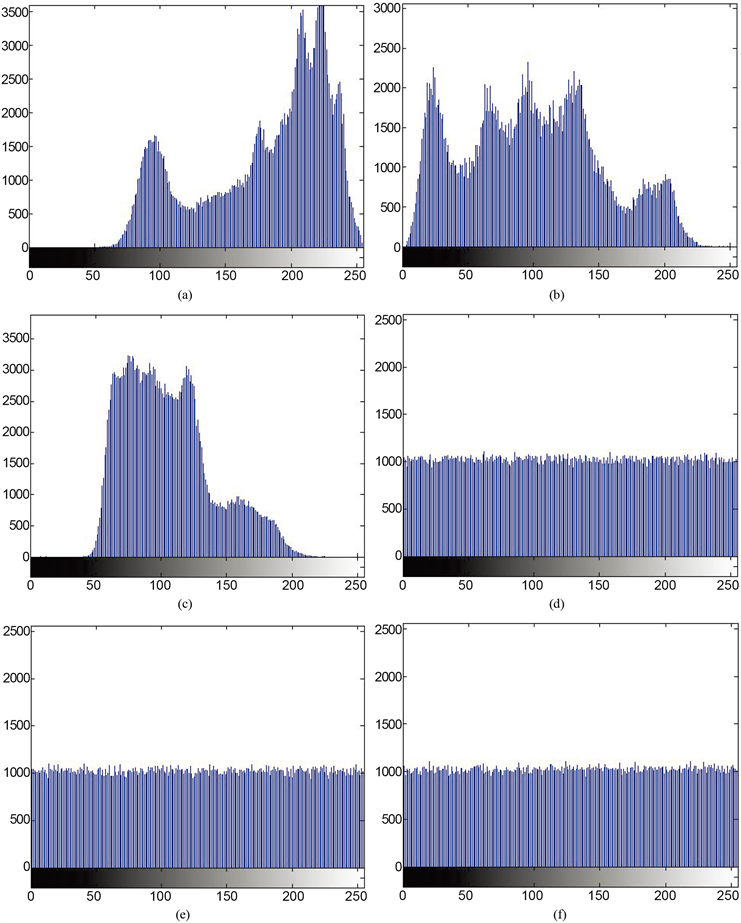
Figure 8. (a)-(f) are the histograms of the red, green, and blue color channels of the Lena plaintext image and its cipher-text, respectively
图8. (a)-(f)分别为Lena明文图像及其密文的红、绿、蓝颜色通道的直方图
这里
是在信息m中
发生的频率或概率,
是指在信息源m中表达一个字符所需要的最基本的bit位个数。对于一个确定和可以预测的信息,由于其每一个元素出现概率均为1,由信息熵的数学定义容易知道该信息的信息熵为0。而对于一个完全随机的序列组成的信息,因为不能预测序列下一个字符的详细情况,所以该信息序列有一个最大的信息熵。对于一幅灰度图像,信息熵定义中的
。一个在0到255范围内一致分布的随机图像,就是说,每个灰度值出现的概率相同,那么由(26)式,可以计算出其信息熵的理想值为8。所以对于图像加密来说,加密图像的信息熵值越接近于8,则图像加密系统泄漏有关明文信息的可能性就越小。类似于彩色图像的直方图分析处理方法,把数字彩色图像的红、绿、蓝 个颜色通道图像矩阵看作为灰度图像矩阵,分别计算明文图像和密文图像每个颜色通道的信息熵值。Lena、Tiffany和Mandrill明文图像及其对应密文图像各颜色通道的信息熵结果如表1所示,可以注意到,密文图像的红、绿、蓝3个颜色通道的信息熵接近于理论值,而明文图像各颜色通道的信息熵则与理论值有明显的差别。为了更好的说明本文提出算法对信息熵攻击是强鲁棒性的,分别采用文献 [19] 和文献 [20] 的算法加密同一幅明文图像,对应的计算结果均列在表1,从表中可以观察到,本文提出算法相比起其他两个算法虽然有微小偏差,但对于不同明文,本文算法的计算结果均接近于理论值,而且在大多数颜色通道上的信息熵值优于其他算法,这就说明了本文提出算法比起其他算法具有更强的抵抗信息熵攻击能力。
4.2.4
. 相邻像素相关性分析
数字图像具有异于其他信息载体的一些固有特性如数据的高度冗余、相邻像素的相关性非常强等,攻击者往往利用这些特性对密文图像进行攻击,所以,一个理想的图像加密算法应该产生在各个方向上(水平、垂直、对角)的相邻像素相关性都非常弱的密文图像。为了量化和比较明文和密文像素在水平、垂直与对角方向的相关性,选取明文Lena图像及其对应本文提出算法密文的各颜色通道分别进行分析比较,分别从各颜色通道上的不同方向随机地选取5000个像素对,并通过式(27)来计算随机选取像素对序列的相关性系数。这里只显示出对明文图像Lena的红色通道及其对应密文的红色通道的分析结果,如表2和图9所示,其他的颜色通道有类似的结果。从表2可以看到,从明文及密文图像红色通道上选取的像素点序列的相关性系数非常地小,几乎接近于0。另外从图9容易观察到,明文图像红色通道的像素点几乎都分布在对角线上,而对应应用本文算法得到的密文图像红色通道上像素点则在平面上呈现遍历状态,且杂乱无章地分布在整个图像平面。以上的量化和比较分析均表明,本文提出的算法成功地消除了相邻像素之间的强相关性,从而使得本文提出的算法具有强鲁棒性
(27)
这里
是指序列
的均值。
4.2.5
. 明文图像与密文图像的相关性
对于一个安全性非常强的图像加密算法,应该能够使加密得到的密文图像与明文图像有非常大的差异,即通过加密算法尽可能地把明文图像的显著特征信息隐藏起来,隐藏越多的信息就意味着明文与密文之间的相关程度越低,这样攻击者对算法的攻击就会变得更加困难。在这里,通过计算Lena明文和密文的红、绿、蓝颜色通道之间的相关系数来分析明文和密文之间的相关性。二维图像矩阵
,
之间的2维相关系数
的数学定义如(28)式所示。二维相关系数的计算结果如表3所示,表中0.0013表示明文绿色通道与密文绿色通道之间的相关系数,其余类似。从表3可以看到明文图像和对应本文算法密文之间的各颜色通道之间的相关性系数都非常小,几乎接近于0,这就说明密文与明文存在很大的差别,明文图像信息几乎完全被隐藏,从而反映了本文提出图像加密算法的有效性。
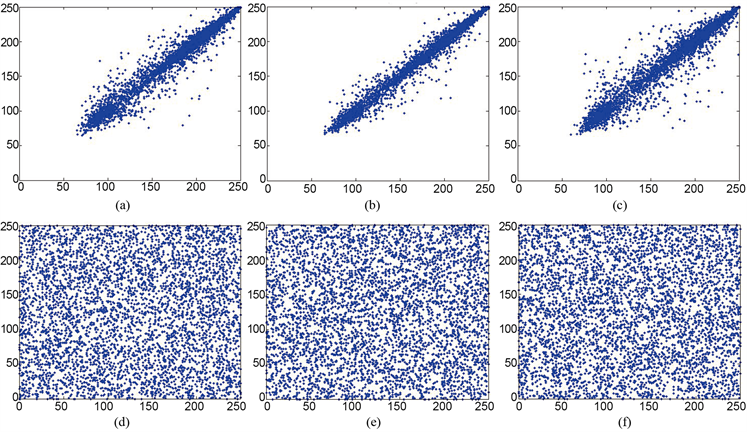
Figure 9. (a)-(c) and (d)-(f) are the distribution of the pixels in the horizontal, vertical and diagonal directions of the red channel of the plaintext and cipher-text
图9. (a)-(c)和(d)-(f)分别是明文和密文的红色通道在水平、垂直和对角方向上的像素点分布

Table 1. The information entropy of each color channel of different plain-texts and cipher-text obtained by using the algorithm proposed in this paper, the literature [19] and [20] algorithm, respectively
表1. 不同明文图像和分别对应本文算法、文献 [19] 、文献 [20] 得到密文图像的各颜色通道信息熵

Table 2. The correlation coefficients between the Lena and its cipher-text red channel in the horizontal, vertical, diagonal direction
表2. Lena及其对应应用本文算法得到密文的红色通道在水平、垂直、对角方向的相关系数

Table 3. The correlation coefficient between the color channels of the plain text and the color channels of the cipher-text
表3. Lena明文与密文的各颜色通道之间相关系数
(28)
在这里
,
分别表示图像矩阵的大小,
表示序列
的均值。
4.2.6. 密钥敏感性分析
一个安全性强的加密算法应该对仅有微小差异的密钥和明文图像都非常敏感 [19] 。一般来说,密钥敏感性分析包括加密方向敏感性分析和解密方向敏感性分析。一方面,由加密算法得到的密文应该对密钥极端敏感,即对密钥仅改变一个单位,那么由同一幅明文加密得到的密文应该与密钥改变前加密得到的密文之间完全没有任何关系或是两个密文之间差别非常地大,而且得到的密文应该不依赖于明文。另一方面,尽管在加密和解密过程的密钥仅有微小差别,但不能够用解密算法来获得正确的明文图像。在这里,先采用密钥
加密Lena明文图像得到密文Image_en,然后对密钥Key仅改变一个单位分别得到如下6个不同的密钥:
,
,
,
,
,
。最后对同一幅Lena图像分别使用上述6个密钥加密得到的结果如图10所示。可以看到,采用不同密钥对同一幅图加密,所产生的密文与Image_en有非常大的差别,甚至是完全不一样的。为了量化不同密文之间的差异性,通过式(28)计算不同密文和Image_en的红(R)、绿(G)、蓝(B)颜色通道之间的相关系数,结果如表4所示,从表中可以注意到,不同密文之间的相关性系数是趋近于0的,从而说明不同密文之间的相关性非常弱。于是从加密敏感性这方面说明了本文提出算法具有极端的敏感性。下面从解密敏感性这方面来说明本文算法的敏感性。用密钥Key和Key1~Key6分别解密密文Image_en,得到的结果如图11所示,可以观察到,只有用正确的密钥才能成功的解密出密文图像,而其他则不能。类似于加密敏感分析,也计算出用不同密钥解密得到的解密文之间的各颜色通道之间二维相关系数,计算结果如表5所示,结果表明本文提出的算法在解密敏感性方面是有效的。
4.2.7. 差分分析
图像加密算法的差分分析是研究在相同加密密钥的条件下密文图像会在多大程度上受明文图像的影响,攻击者通常通过选择明文分析或选择密文分析来实现差分攻击。为了测试本文提出图像加密算法抵抗差分攻击的能力大小,采用两个常用的度量指标:不同密文图像之间的像素改变率(number of piexls change rate, NPCR)和一致改变强度(unified average changing intensity, UACI),其数学公式定义如下:
(29)
(30)
 (a)
(a)  (b)
(b)  (c)
(c)  (d)
(d)  (e)
(e)  (f)
(f)  (g)
(g)  (h)
(h)  (i)
(i)  (j)
(j)  (k)
(k)  (l)
(l)
Figure 10. (a), (c), (e), (g), (i), (k) are cipher-text using algorithm proposed encrypted by Key1 - Key6, respectively, (b), (d) (f), (h), (j), (l) correspond to the differences between (a), (c), (e), (g), (i), (k) and Image_en, respectively
图10. (a),(c),(e),(g),(i),(k)分别为Key1~Key6应用本文提出算法得到的密文,(b),(d),(f),(h),(j),(l)分别对应(a),(c),(e),(g), (i),(k)与Image_en的差

Table 4. The correlation between the red (R), green (G), and blue (B) color channels of the cipher-texts encrypted with different keys and Image_en
表4. 用不同密钥加密得到的密文和Image_en的红(R)、绿(G)、蓝(B)颜色通道之间的相关系数
注:CRR是指用Key1加密得到密文的R通道与Image_en的R通道之间的相关系数,其余类似。

Table 5. The correlation coefficients of the red (R), green (G), and blue (B) color channels between the decrypted text and the plaintext Lena obtained using different keys
表5. 采用不同密钥得到的解密文和明文Lena之间的红(R)、绿(G)、蓝(B)颜色通道的相关系数
注:CRR是指用Key1解密得到解密密文的R通道与Lena明文的R通道之间的相关系数,其余类似。
(31)
这里
,
分别是图像矩阵的大小,
是表达一个像素值所需要的bit个数,对于灰度图像,
。
,
分别是明文图像改变前后得到对应应用本文提出算法得到的密文。对于一个灰度图像,NPCR,UACI的理想估计值分别为99.6094%,33.4636% [20] 。对于明文Lena图像的每个颜色通道,随机地选取的100个像素值,对每个灰度值仅随机改变1bit像素值,然后用本文提出加密算法去加密改变前后的明文图像Lena,得到对应每个颜色通道的100个NPCR,UACI曲线变化图如图12所示,从图中可以看到每个颜色通道的NPCR,UACI值均在理想值上下波动,红、绿、蓝各颜色通道的100个NPCR,UACI的最大值、最小值和均值如表6所示,很明显,这些值是非常接近理想估计值,另外,类似于上述做法,计算出了文献 [19] 和 [20] 的NPCR和UACI的均值也如表6所示,不同算法比较可知,本文提出算法抵抗差分攻击的能力是强鲁棒的。

Figure 12. (a)-(c) and (d)-(f) are the NPCR and UACI curves of the cipher-text obtained before and after the change of the plaintext image, respectively
图12. (a)-(c)和(d)-(f)分别是明文图像改变前后得到的密文之间的NPCR和UACI变化曲线
4.2.8. 已知明文和选择明文攻击分析
很多图像加密算法已经被选择明文和已知明文攻击 [25] ,于是对于一个理想的图像加密算法应该能够抵御这样的攻击。在本文提出的算法中,采用预先扩散–置乱–扩散机制对明文图像进行加密,在预处理阶段的扩散过程采用由改进一维混沌系统产生的初始向量对明文图像进行预处理,使得当密钥仅发生微小的变化,就会引起初始向量的完全不同,从而使得预处理后的图像依赖于明文图像。另一方面,在最后的扩散阶段对每一个图像像素灰度值均基于动态反馈式的扩散,说明在这一阶段极端依赖于预处理后的图像,从而使得整个加密算法是依赖于明文的,于是本文提出的加密算法是能够抵抗已知明文和选择明文的攻击的。为了从实验上来验证提出加密算法抵抗已知明文和选择明文的有效性。选择全黑的明文图像,利用本文提出的加密算法和密钥Key分别进行加密得到其密文图像。明文和密文及其各自的每个颜色通道上直方图如图13所示,除此之外,还计算出全黑和全白及其对应密文的各颜色通道之间的信息熵,结果如表7所示,从图13和表7可以看到,本文提出的加密算法能够很好地抵抗选择明文和已知明文攻击。

Table 6. The maximum, minimum, and average values of the NPCR and UACI sequences between the corresponding cipher-texts before and after the Lena image changes (%)
表6. Lena图像改变前后对应密文之间的NPCR和UACI序列的最大值、最小值和平均值(%)
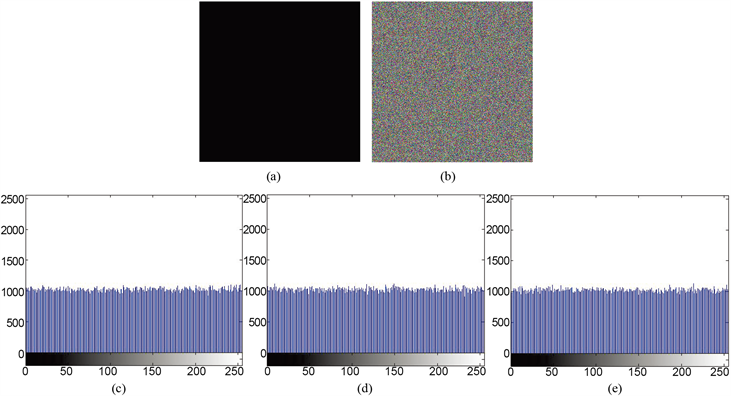
Figure 13. b), (c), (d), and (e) are the cipher-text and the distribution histograms of its red, green and blue color channels
图13. (b),(c),(d),(e)分别是明文(a)对应本文提出算法加密得到的密文及其红、绿、蓝颜色通道的分布直方图

Table 7. The information entropy of the red, green and blue color channels of cipher-text obtained by the algorithm encrypting all black and white plain images
表7. 全黑和全白明文图像对应本文提出算法加密得到密文的红、绿、蓝颜色通道的信息熵
5. 总结
本文提出基于一维混沌映射和类标准映射的彩色图像加密算法。首先由两个改进一维映射构造出新的类标准映射并通过空间相位图、Lyapunov指数和时间序列测试对其混沌性质进行分析,分析表明构造的新类标准映射是混沌的且具有良好的随机性。然后基于一维混沌映射和类标准映射设计了一种彩色图像加密算法,不同于传统置乱–扩散机制,该算法采用预先扩散–置乱–扩散结构,在预先扩散阶段利用一维映射产生初始向量对明文图像进行预处理,然后采用新构造的类标准映射产生随机数对预处理后的图像进行加密。最后有关本文提出算法的重要安全性能分析被提出,包括密钥空间分析、密钥敏感性分析和统计分析等,所有的实验结果均表明,本文提出算法具有较强的鲁棒性,因而具有一定的应用价值。