1. 引言
由于图像的细微改变不会引起人类视觉系统的感知,因此利用图像的视觉冗余,把秘密信息嵌入到图像中,而不影响图像的视觉效果。例如,水印 [1] 、认证 [2] 、隐写 [3] [4] [5] ,水印是为了保护载体的所有权,认证是为了数据的完整性,而隐写是为了秘密信息的传输。
近年来,由于网络的迅速发展,给信息的传输带来了方便,而网络上的图像无处不在,在图像上隐藏秘密信息成了新的热门研究领域。最经典的图像信息隐藏方法之一是基于像素差的信息隐藏算法,基于像素差的信息隐藏算法 [6] [7] [8] [9] [10] 主要是考虑两个相邻像素的像素差,由于视觉系统对纹理丰富区域的像素的改变不太敏感,因此基于像素差的信息隐藏算法在纹理丰富区域嵌入的信息比平滑区域要多。
最初的基于像素差的信息隐藏算法是由Wu和Tsai [6] 于2003年提出。然而此算法使得图像的像素值的修改幅度较大,嵌入失真度较大,相对应的载密图像像素差的直方图偏离原始图像的直方图较大。为了改进基于像素差的信息隐藏算法,2008年,Wang等人 [7] 应用模函数在图像的边缘区域嵌入更多的秘密信息(MF-PVD),不过此算法却使得像素差值直方图在零附近急剧变化,比较容易被基于直方图分析检测到。Yang等人 [10] 也于2008年提出了一种改进的边缘区域的像素差的信息隐藏算法(AE-PVD),这种算法优于最初的PVD算法。AE-PVD选择两个像素作为一个嵌入单元,算出两个像素差的绝对值,嵌入的秘密信息比特数由像素差的绝对值决定,像素差的绝对值在嵌入前后属于相同的划分区,才能保证秘密信息的正确提取。与PVD隐藏算法相比,MF-PVD和AE-PVD嵌入相同的秘密信息时,能保持更好的图像质量。然而,AE-PVD算法采用最优像素调整算法(OPAP)嵌入秘密信息,比较容易被卡方分析检测到;另外,AE-PVD算法引起像素差直方图的异常变化,因此也难以抵抗基于像素差的直方图分析。2010年,Joo等人 [8] 改进了MF-PVD算法,能抵抗直方图的分析,不过图像的质量比AE-PVD差,不适合于特殊的应用,如军事,医用图像等。同年,Yoo等人 [11] 改进了MF-PVD算法,考虑图像的局部特征及人类视觉系统,他们首先把图像分成大小为4 × 4的像素块,然后获得每个像素块像素的高频部分,由于人类视觉对高频系数的变化不太敏感,所以在高频部分能嵌入更多的秘密信息。可是,他们也是应用OPAP算法嵌入信息,卡方分析能检测出图像中是否嵌入秘密信息。
2008年,Chang等人 [12] 提出了基于三个不同方向像素差的信息隐藏算法(TPVD),此算法不仅提高了嵌入秘密信息的容量而且也能使嵌入信息后的图像具有很好的视觉掩蔽性。此外,Jung等人 [13] 提出用多重像素差来估计每个像素的平滑程度。Balasubramanian等人 [14] 提出了一种新的像素差信息隐藏算法,此算法考虑八个方向的像素差。Jung和Yoo [15] 提出了一种基于索引函数,利用像素差嵌入信息的算法,此算法中的索引函数提高了嵌入秘密信息的安全性,嵌入每个图像的容量也较大。然而,此算法中的索引函数要么所选择的像素块中的参考像素的位置在整个图像中是一样的,要么就得选择一定的存储空间来保存索引函数值。
虽然已经有很多关于像素差信息隐藏算法,但仍有一定的研究空间,考虑如果去提高嵌入容量,减少图像的失真。本文提出了一种基于像素差和索引函数的信息隐藏算法,改进了Jung和Yoo [15] 提出的索引函数,使得选择像素块中的参考像素更具有一定的随机性,从而嵌入信息后的图像更具有安全性。
2. 预备知识
把图像分成互不重叠的大小为
像素块
,其中N表示像素块的总块数。每个像素块中含有
像素
,其中
分别表示像素
在像素块中所在的行与列。则索引函数定义如下:
(1)
由于本文信息隐藏算法中参考像素是由索引函数决定的,攻击者如果没有索引函数,很难知道哪个像素是参考像素,信息隐藏算法更具有安全性。确定了参考像素,然后计算其与周围像素的像素差。
例如,
是
像素块中的四个像素,有
通过公式(1),就能确定每个像素块中哪个像素作为参考像素。将像素值的范围[0,255]划分成7个连续子区间
,即
(2)
每个子区间
的上、下界、宽度分别为
和
其中宽度
。找到像素差的绝对值
所属的子区间
,如果
。从二进制信息比特流截取
位秘密信息,把
的二进制秘密信息比特流转换成十进制下的数
。
2.1. 秘密信息嵌入算法
首先由索引函数选择每个子像素块中哪个像素作为参考像素,然后计算参考像素与其周围的其它像素的差,根据像素差所处的范围值确定嵌入秘密信息的长度。详细的嵌入过程如下:
1) 把图像分成互不重叠的大小为
的像素块
,其中t是表示像素块所在的位置。
2) 如果
,则选择
作为参考像素,然后根据下面的公式将参考像素值量化
(3)
3) 计算每像素块中量化后的参考像素跟其周围像素值的差
(4)
表示第
块像素块中的像素值。
4) 若
属于
,则嵌入的秘密信息的比特数为
。
5) 应用余函数减少像素差的变化,降低图像的失真率。对每个像素差除以
,得到相应的余数,这样所得到的余数比原来的像素差的值要小,从而降低因嵌入秘密信息引起的图像失真率。具体计算公式如下:
(5)
6) 从二进制比特流中读取
位秘密信息,把其转换成十进制的数
。例如,如果截取的二进制比特流是101,转换成十进制数为5。
7) 用秘密信息的值减去余数得新差值
(6)
令
(7)
其中
是十进制的秘密信息值。
8) 为了嵌入信息后减少对图像的失真,应用下列的改变像素值的最佳嵌入算法:
情况1:
和
和
;
(8)
情况2:
和
和
;
(9)
情况3:
和
和
;
(10)
情况4:
和
和
;
(11)
情况5:
和
和
;
(12)
情况6:
和
和
;
(13)
情况7:
和
和
;
(14)
情况8:
和
和
;
(15)
9) 像素调整。少数情况下,通过上述的秘密信息嵌入,像素值
超出像素值的范围[0,255],即
或
。如果出现这种情况,
通过下列最优方式进行调整,寻找符合下列四个条件的像素值
替换
:
a)
和
属于同一个范围,其中
和
分别表示嵌入信息前后两像素的差,
b)
;
c)
最小;
d)
。自此,实现了在该像素上嵌入秘密信息。
10) 重步骤(2)-(9),直到所有的秘密信息都被嵌入到图像中,得到嵌入后的载密图像。
2.2. 秘密信息提取算法
这一小节描述提取秘密信息的详细过程。先把载密图像分成互不重叠的大小为n × n的像素块,每像素块的处理跟嵌入过程一样:按索引函数确定像素块中的参考像素,然后计算参考像素与其周围像素的差,由差值所处的范围值确实嵌入的秘密信息的比特位。详细的提取信息过程如下:
1) 把载密图像分成互不重叠大小为
的像素块
;
2) 如果
,则选择
作为参考素
,对参考像素值进行量化
(16)
3) 计算每像素块中参考像素量化后的值与其周围像素值的差
(17)
其中
表示第t块像素块中除参考像素外其它的像素值;
4)
属于
,则嵌入的秘密信息的比特数为
;
5) 计算像素值差
与
所得的余数就是嵌入的秘密信息
(18)
最后,把
转换成
比特位的二进制信息流,于是,嵌入到载体中的秘密信息被提取了。
3. 举例
这一节我们以图1作为例子,把原始图像分成
的像素块。
3.1. 举例说明秘密信息嵌入
不妨假设
,则由
可知,选择的参考像素是
。接着由等式(3)量化参考像素值
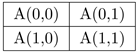

 (a) (b) (c)
(a) (b) (c)
Figure 1. The embedding process. (a) Index function; (b) Original image; (c) Stego-image
图1. 嵌入过程。(a) 索引函数;(b) 原始图像;(c)载密图像
根据等式(4),算出量化后的参考像素值与其周围像素值的差:
所以,我们有
然后,由式(5)可得:
若秘密信息二进制比特流为
,把它们转换成十进制的数
因此,利用等式(6),获得像素块新的差值:
同时由等式(7),有
由秘密信息嵌入过程中的第八步骤,得到像素块中新的像素值:
因为
和
都属于
,因此,我们有
自此,秘密信息已成功的嵌入到原始图像中。
3.2. 举例说明秘密信息提取
若
,则我们由
选择参考像素值
。首先,我们应用等式(16)量化参考像素值,得
进一步由等式(17)获得像素差:
因此,可得
同时,根据等式(18),很容易可得到
最后,把这些十进制的数转换成二进制的比特流,
。所以嵌入的秘密信息为
。由此可知,嵌入的秘密信息能完全正确的提取出来。
4. 实验结果与比较
本节将给出实验对比结果来验证改进算法的有效性。实验中用8幅大小为
经典灰度图像(“Lena”, “Peppers”, “Baboon”, “House”, “Boat”, “F16”, “Man”, “Elaine”)作为载体图像。图2给出了这8幅灰度图像,用伪随机数发生器生成的一串伪随机数字当作秘密信息嵌入到载体图像中。
图2给出了实验的八幅原始图像与载密图像,其中图2(a),图2(c),图2(e),图2(g),图2(i),图2(k),图2(m),图2(o)是原始图像,图2(b),图2(d),图2(f),图2(h),图2(j),图2(l),图2(n),图2(p)是载密图像。实验结果表明,本文所提出的算法当嵌入秘密信息后,不会影响图像的视觉效果,人的肉眼很难分辨出哪是原始图像,哪是载密图像。
图3给出了本文算法嵌入秘密信息比特数与提取的错误率之间的关系,从图中可以进一步得出,本文所提出的算法能把嵌入的秘密信息完全提取出来,即提取的错误率为零。

Figure 2. The eight test images. (a) Original image; (b) Stego-image; (c) Original image; (d) Stego-image; (e) Original image; (f) Stego-image; (g) Original image; (h) Stego-image; (i) Original image; (j) Stego-image; (k) Original image; (l) Stego-image
图2. 八幅实验图像。(a) 原始图像;(b) 载密图像;(c) 原始图像;(d) 载密图像;(e) 原始图像;(f) 载密图像;(g) 原始图像;(h) 载密图像;(i) 原始图像;(j) 载密图像;(k) 原始图像;(l) 载密图像
用峰值信噪比(Peak Signalto Noise Ratio,简称PSNR)来评估载密图像的图像质量。本文算法的实验结果由表1给出,表1中,“容量”表示的嵌入的秘密信息的比特数,“PSNR”为峰值信噪比值,“错误”为错误提取秘密信息比特数,“嵌入(秒),提取(秒)”分别为本文所提出的算法嵌入和提取信息所需要的时间。表1概述了本文所提出的算法的实验结果。实验结果也表明,本文所提出的算法能把嵌入后的秘密信息完全提取出来,而且嵌入和提取所需要的时间很少。
 (a)
(a) 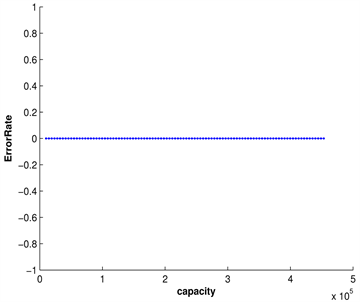 (b)
(b)
Figure 3. The error rate and the number of bits of the experiment results. (a) Peppers; (b) Lena
图3. 提取错误率与嵌入容量。(a) Peppers; (b) Lena

Table 1. The experiment result in our proposed method
表1. 本文算法的实验结果
从表2可以看出,虽然本文的算法与其它两种算法相比较,载密图像的PSNR值有所下降,可嵌入容量比Wu和Tsai算法 [6] 和Wang等的算法 [7] 分别高出44,168~191,086 bits,38,507~171,787 bits。较高的嵌入容量说明本文的算法能更好的区分图像的平滑区域与边缘区域,例如纹理比较丰富的Baboon图像,嵌入容量比Wu和Tsai算法 [6] 和Wang等的算法 [7] 分别高出191,086 bits和171,787 bits。而且从嵌入的容量来看,不同的图像嵌入容量相差比较大,边缘越丰富的图像嵌入的容量就越多。说明了本算法充分考虑了图像不同的区域承受的像素差的变化不一样,充分考虑了图像的视觉效应。
从表3可以看出,Jung和Yoo的算法虽然嵌入容量比本文的算法要高,可选择了六幅不同的图像,由于没有充分考虑图像的平滑区域与边缘区域对像素变化的承受力的不同,它们的嵌入容量非常的接近。同时,Jung和Yoo的算法嵌入信息后,对图像造成了一定程度的失真,其PSNR值大部分都低于30 dB,其中最低的PSNR值只有25.96 dB。
表4是比较本文算法和Lee等的算法,Zeng等的算法的PSNR值和有效嵌入量,从表4可看出,本文的算法不仅有效嵌入量比他们的高,同时也能很好的保证载密图像的质量,即嵌入信息后造成的图像的失真程度较低。

Table 2. Comparisons of other method and our proposed
表2. 本文算法与其它算法的实验结果比较
*注:上标1:表示Wu和Tsai的算法 [6] 实验结果,上标2:表示Wang的算法 [7] 实验结果,上标3:表示本文的实验结果

Table 3. Comparisons of other method and our proposed
表3. 本文算法与其它算法的实验结果比较
*注:上标1:表示Yang和Yoo的算法实验结果,上标2:表示本文的实验结果

Table 4. Comparisons of other method and our proposed
表4. 本文算法与其它算法的实验结果比较
*注:上标1:表示Lee和Chen的算法 [16] 实验结果, 上标2:表示Wang的算法 [17] 实验结果,上标3:表示本文的实验结果
表5是本文的算法与Hong [18] 提出的几种不同的划分区域的算法相比较。从表4可以看出,本文算法的平均嵌入容量分别比Hong提出的AE-PVD (D12 = 15),PRT-PVD (T0 = 15),AE-PVD (D12 = 15,D23 = 31),PRT-PVD (T0 = 15,T1 = 15)多出196,955 bits,190,980 bits,181,891 bits,172,650 bits。如边缘比较丰富的Baboon图像,本文的算法分别比Hong提出的AE-PVD(D12 =15),PRT-PVD (T0 =15),AE-PVD (D12 = 15,D23 = 31),PRT-PVD (T0 = 15,T1 = 15)多出261,314 bits,261,684 bits,207,509 bits,209,314 bits。即使是平滑的图像Lena,本文的算法也分别比Hong提出的AE-PVD (D12 = 15),PRT-PVD (T0 = 15),AE-PVD (D12 = 15,D23 = 31),PRT-PVD (T0 = 15,T1 = 15)多出177,045 bits,168,797 bits,173,616 bits,161,525 bits。虽然,Hong的算法也考虑了根据像素差来决定嵌入的秘密信息的比特数,可其划分的区域

Table 5. Comparisons of other method and our proposed
表5. 本文算法与其它算法的实验结果比较
*注:上标1:表示AE-PVD (D12 = 15)算法实验结果, 上标2:表示PRT-PVD (T0 = 15)实验结果,上标3:表示AE-PVD (D12 = 15;D23 = 31)实验结果,上标4:表示PRT-PVD (T0 = 15;T1 = 15)实验结果,上标5:表示本文的实验结果
相对而言比较粗糙,不能完全真实的反应图像的区域特征。虽然本算法的PSNR值比Hong提出的几种算法低,可也能使图像的PSNR保持在30 dB上。
PSNR值是最常用来检测嵌入信息后的载体图像质量,通过PSNR值的大小,我们可很清楚的知道嵌入信息后的图像是否会被人的肉眼观测出来。然而,PSNR值不能指出嵌入信息前后两幅图像之间差别有多大。因此,应用由Wang和Bovik [19] 提出的通用质量因子Q值来检测图像在嵌入信息前后的相似度有多高,并指出Q值的范围是从−1到1。Q值越接近于1,说明嵌入信息前后的两幅图像越相似。由表6所给出的数据,可知通过本文算法进行信息隐藏,所得的Q值非常的接近1,也就是说嵌入信息前后原始图像与载密图像非常的相似。
所有的实验结果都表明,本文所提出的信息隐藏算法不仅有着很高的嵌入容量,而且也能保持很小的图像失真。由于嵌入信息后,图像失真很小,因此,即使非法者拥有了载密图像,他们也区分不了载密图像与原始图像,不知道载密图像中已经隐藏了秘密信息,也就是说本文所提出的算法能很好的隐藏信息已经嵌入到图像中去这样的事实。
5. 分析和讨论
5.1. RS分析
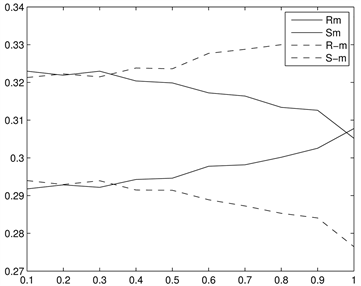
Fridrich等人 [20] 提出的RS分析算法来分析本文所提出的信息隐藏算法的安全性。RS分析本文所提出的信息隐藏算法的结果在图4中给出,其中是以图2中的一幅图做实验。图4中的x-轴表示嵌入秘密信息容量的百分比,y-轴表示掩膜为
和
,正则组与奇异组的百分比。从图4(a)和图4(c)我们可以看出RS分析能检测出图像经过了LSB信息隐藏,这是因为随着LSB嵌入率到达100%时,
和
的差距会随着密写率的上升而下降,而
和
与原始值之间就会偏离得更远。但图4(b)和图4(d)载体图像看似不包含任何嵌入秘密信息的嵌入,这是因为在图4(b)和图4(d)中
和
始终近似相等,而
和
值亦如此,也就是说
和
。因此,可以肯定的说,本文所提出的信息隐藏算法抗RS分析。
5.2. PVD直方图分析
Zhang和Wang [21] 指出文献 [22] 所提出的一种基于相邻像素对差异的PVD信息隐藏算法导致了像素灰度差值直方图的异常,存在安全漏洞。通过基于PVD的直方图的分析,可以检测和分析出图像中是否隐藏了秘密信息。
 (a)
(a) 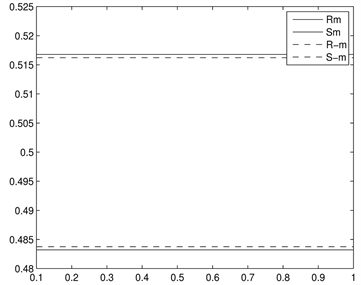 (b)
(b)  (c)
(c) 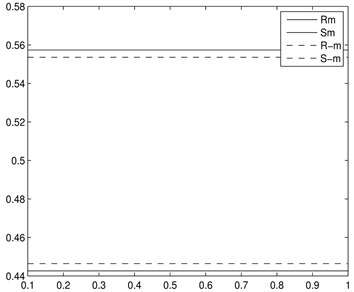 (d)
(d)
Figure 4. RS-diagrams yielded by the dual statistics method by Fridrich et al. for cover images produced by conventional LSB-embedding technique and our method. (a) LSB (Baboon); (b) our proposed (Baboon); (c) LSB (Peppers); (d) our proposed (Peppers)
图4. 应用RS分析LSB嵌入信息算法与本文所提出的嵌入信息算法。(a) LSB (Baboon); (b) 本文算法(Baboon); (c) LSB (Peppers); (d) 本文算法(Peppers)

Table 6. The experiment result in our proposed method
表6. 本文算法的实验结果
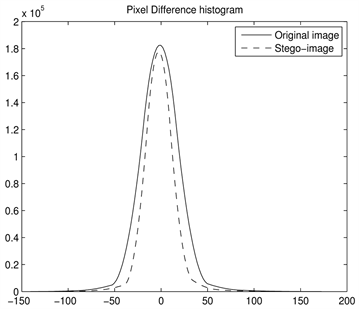
图5给出了PVD直方图分析本文所提出的信息隐藏算法在嵌入容量最大时的原始图像与载密图像的直方图,图5(a)和图5(b)给出的是灰度图像“Baboon”和“Peppers”像素差的直方图。从图5可以看出本文所提出的基于像素差和索引函数的信息隐藏算法抗PVD直方图分析,也就是说可以完好隐藏嵌入的秘密信息。
 (a)
(a) 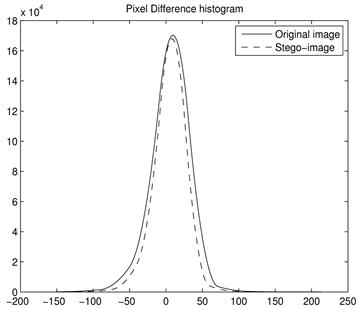 (b)
(b)
Figure 5. PVD histogram differences between covers and theirs corresponding stegos. (a) F16; (b) House
图5. 由原始图像和载密图像得到的灰度差值直方图。(a) F16; (b) House
6. 本文小结
本文提出了一种基于像素差和索引函数的信息隐藏算法,首先把原始图像分成互不重叠的像素块,然后根据索引函数确定每个像素块中的参考像素。由参考像素跟它周围的其它像素的差来决定嵌入的信息的比特数。本文所提出的索引函数改进了Jung等人提出的索引函数,Jung等人提出的索引函数,要么就是所有的像素块中做为参考像素的位置是一样的,要么就得有一定的存储空间来保存索引值,而本文所提出的索引函数具有更好的随机性,即使非法截者获得了载密图像,如果他们没有索引函数也不能正确的提出秘密信息,因此索引函数起到了一种密钥的作用。实验表明,本文提出的算法有较高的嵌入容量和保持好的图像质量。
基金项目
国家自然科学基金面上项目(11571124,61572028),2016年广东省应用型科技研发专项资金项目重大专项(2016B020244003),佛山市科技创新项目–高校和医院科研基础平台建设项目(2014AG100162),华南师范大学青年教师科研培育基金项目(15KJ06)。
NOTES
*通讯作者。